Registering Single Tenant in Organizational Directory
This section describes how to register access to OVOC for operators from a single organizational tenant in the Organizational directory. For this deployment operators retrieve their security level from OVOC through a mapped Azure security group. A security group must be defined on Azure for each required security level. You must then assign operators to the relevant group accordingly. After performing this procedure, add the Azure groups and their operator members (see Create Azure Groups and Assign Members). These groups are mapped to OVOC for retrieving the operator security levels.
| ➢ | Do the following: |
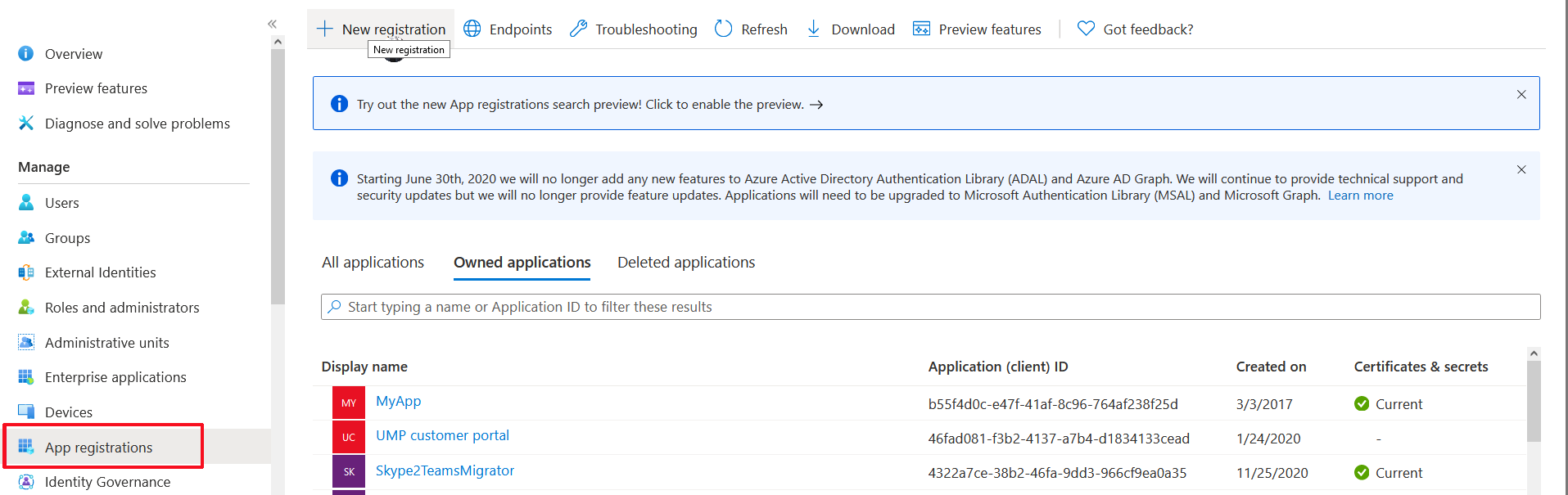
| 1. | Login to the Azure portal with tenant admin permissions. |
| 2. | In the Navigation pane, select App registrations and then click New registration. |
App registrations
| 3. | Enter the name of the OVOC registration tenant. |
| 4. | Select Accounts in this organizational directory only (Tenant name- Single tenant). |
Single Organizational Tenant
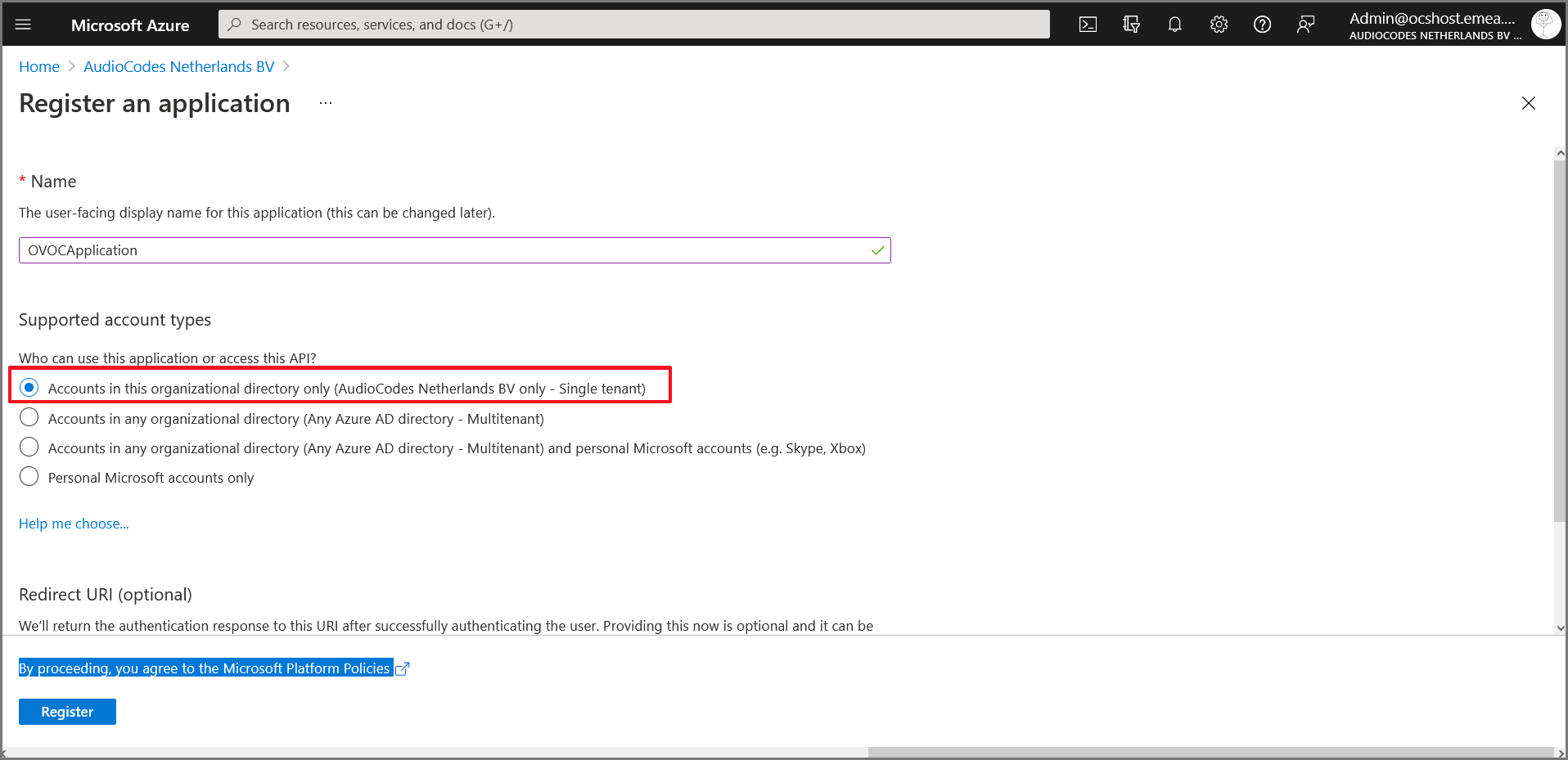
| 5. | Enter the HTTPS Redirect URI (REST endpoint) for connecting to OVOC Web in the following format: |
https://x.x.x.x/ovoc/v1/security/actions/login
Register an application

| 6. | Click Register. |
The new registered application is displayed.
New Registered Application
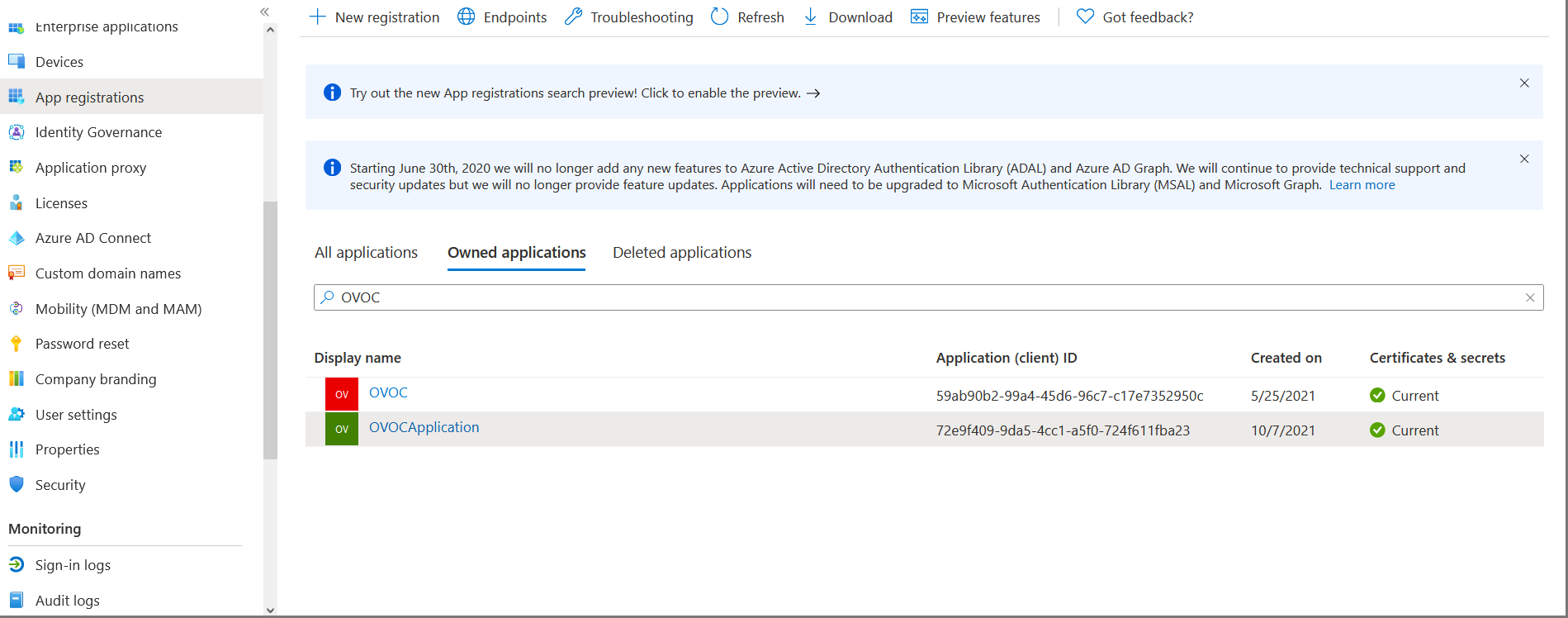
| 7. | Double-click the new application i.e. OVOCApplication (in this example) to configure it. |
| 8. | In the navigation pane, select Certificates & secrets. |
Certificates & secrets
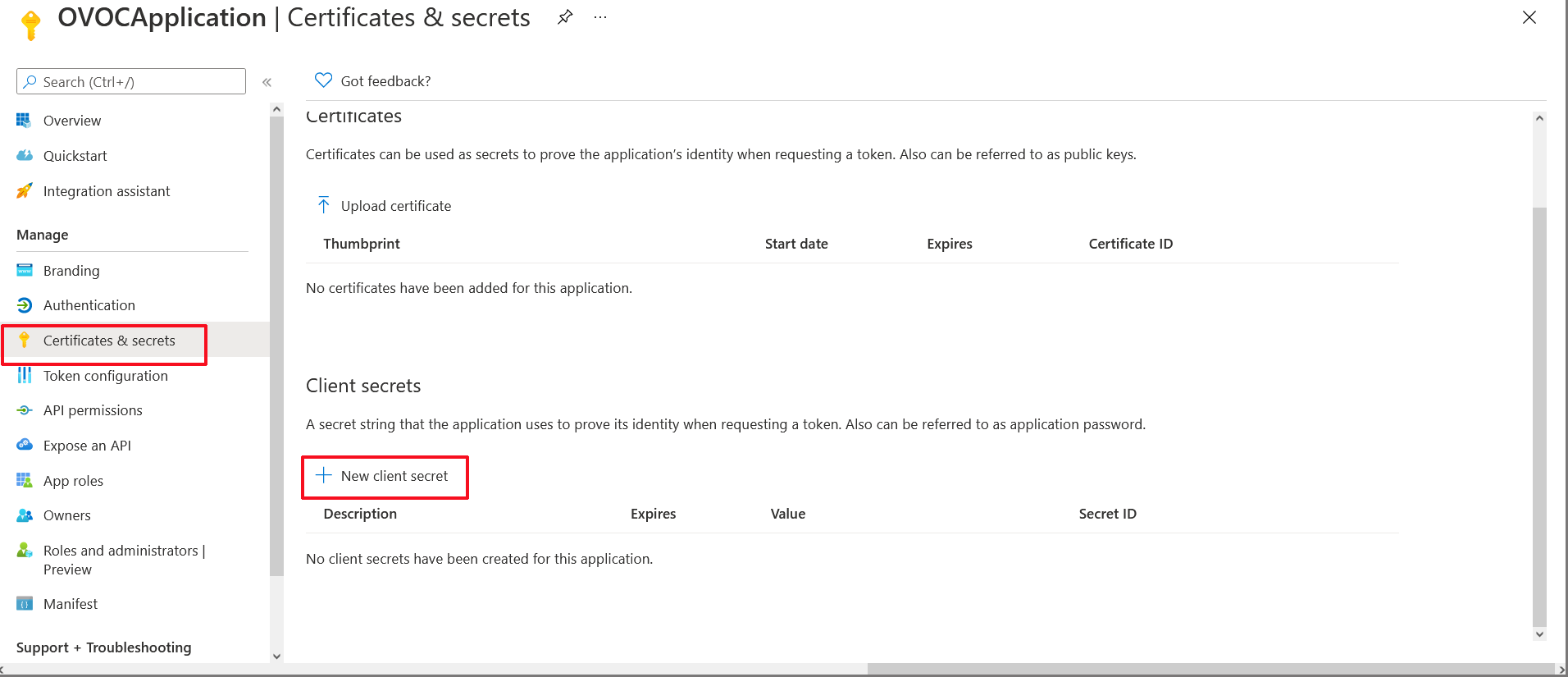
| 9. | Click New client secret. |
New client secret
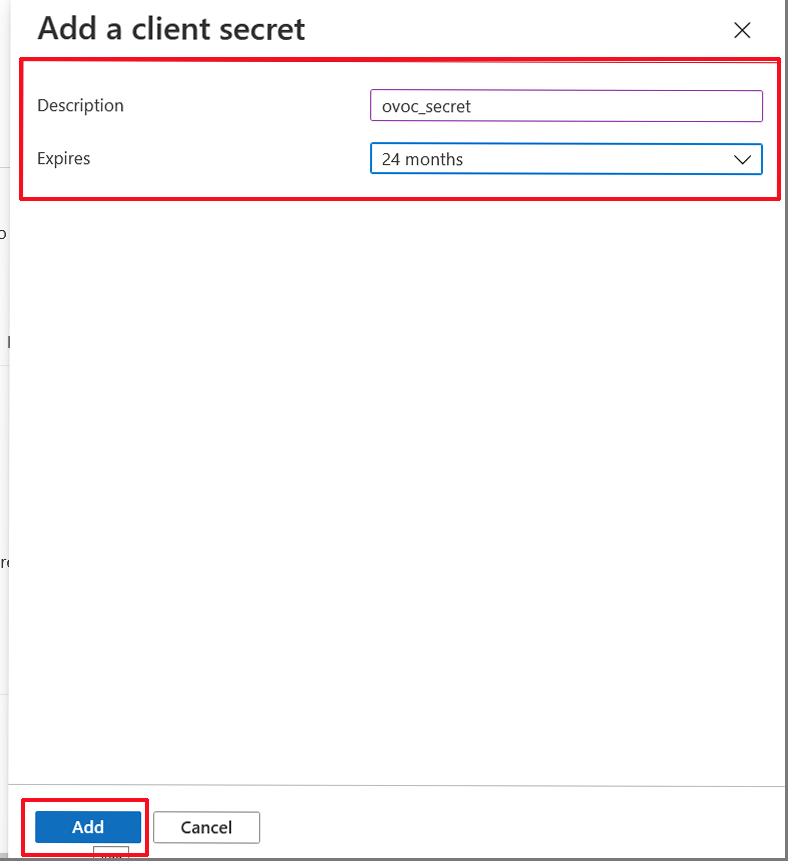
| 10. | Enter a description and from the drop-down list select 24 months. |
| 11. | Click Add. |
Client Secret Generated
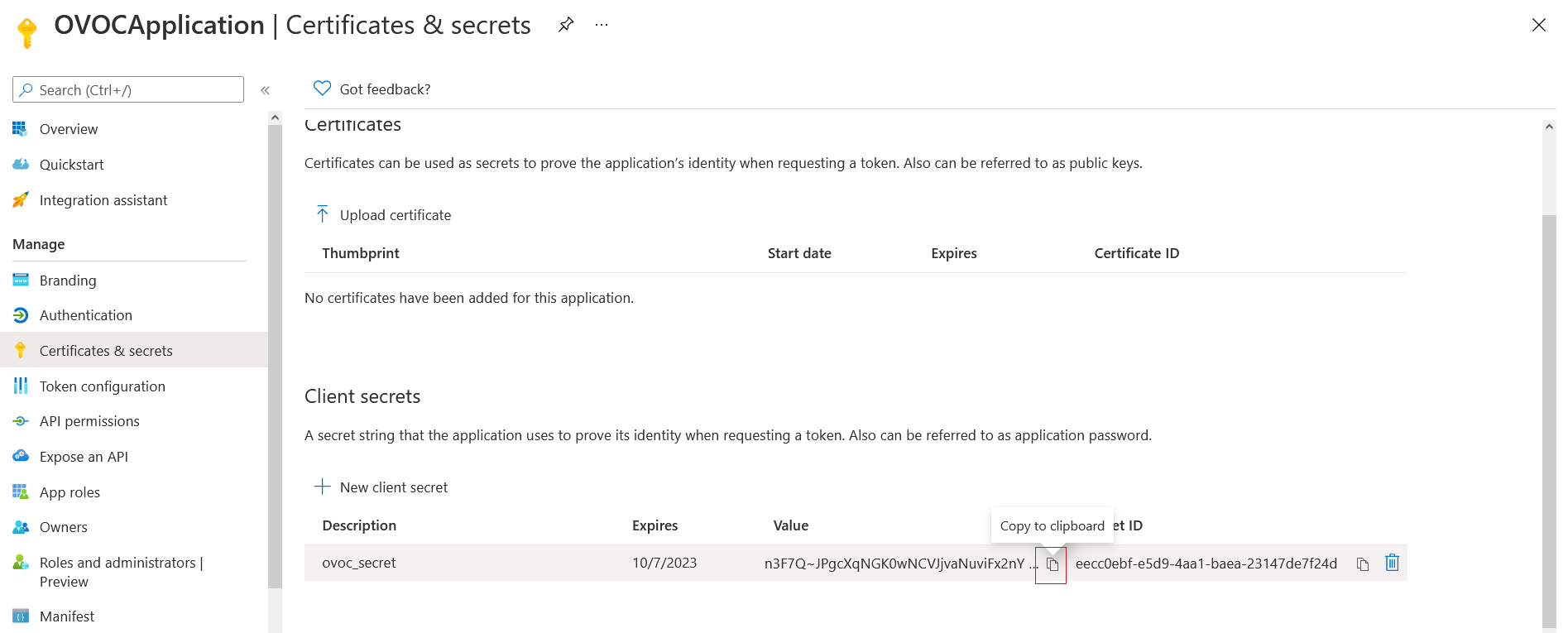
| 12. | Copy the secret Value to clipboard as its required in later configuration and cannot be retrieved once you leave this screen. |
| 13. | In the navigation pane, select Authentication. |
Authentication
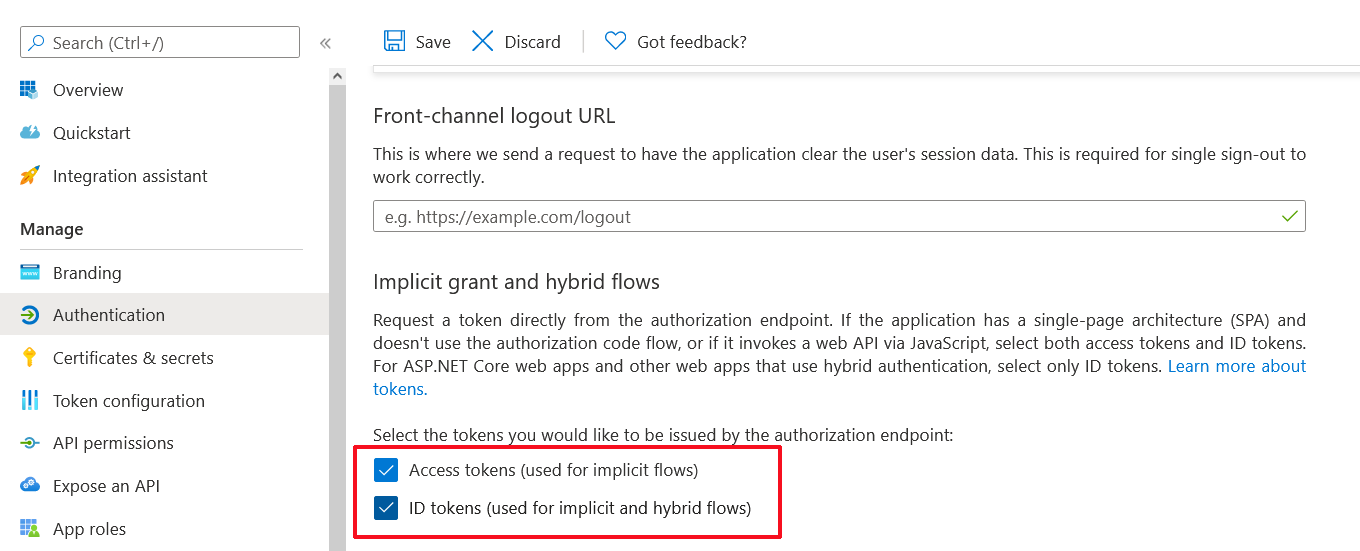
| 14. | Under Implicit grant and hybrid flows select the following: |
| ● | Access tokens (used for implicit flows) |
| ● | ID tokens (used for implicit and hybrid flows) |
| 15. | Click Save. |
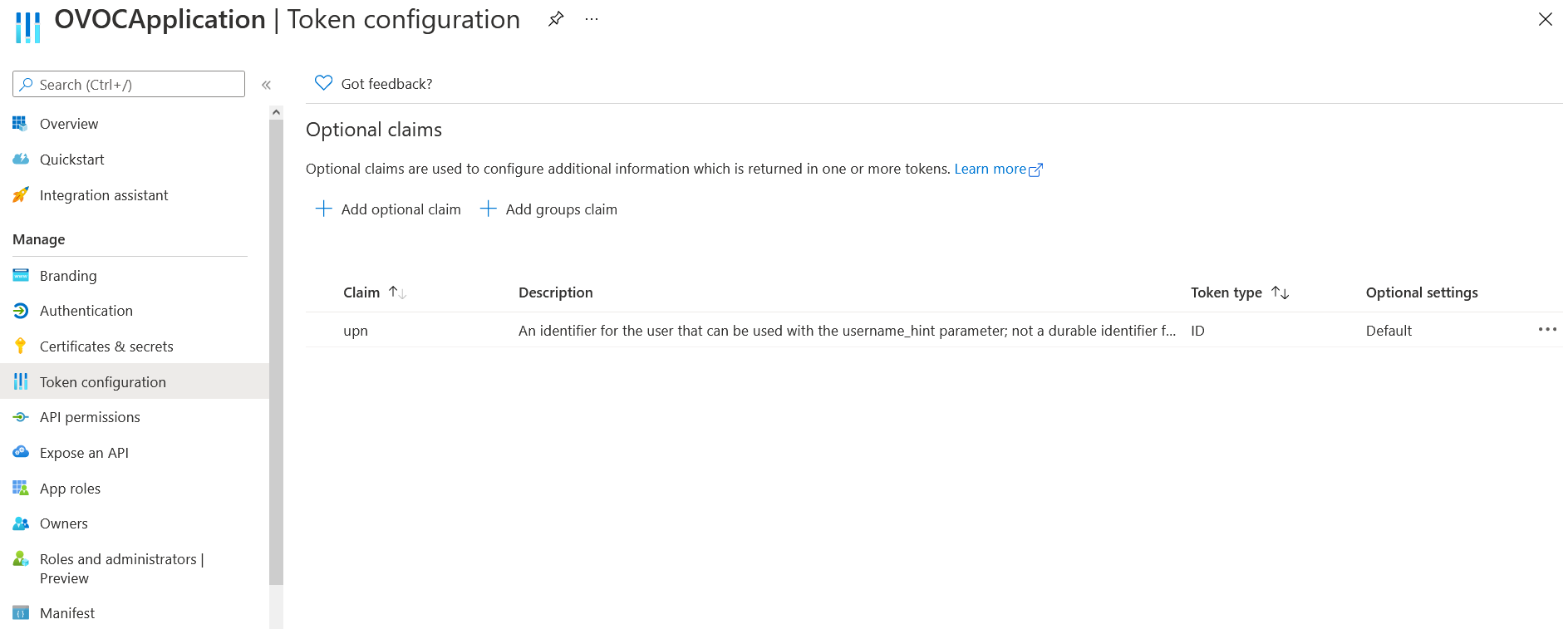
| 16. | In the navigation pane, select Token configuration. |
Token configuration
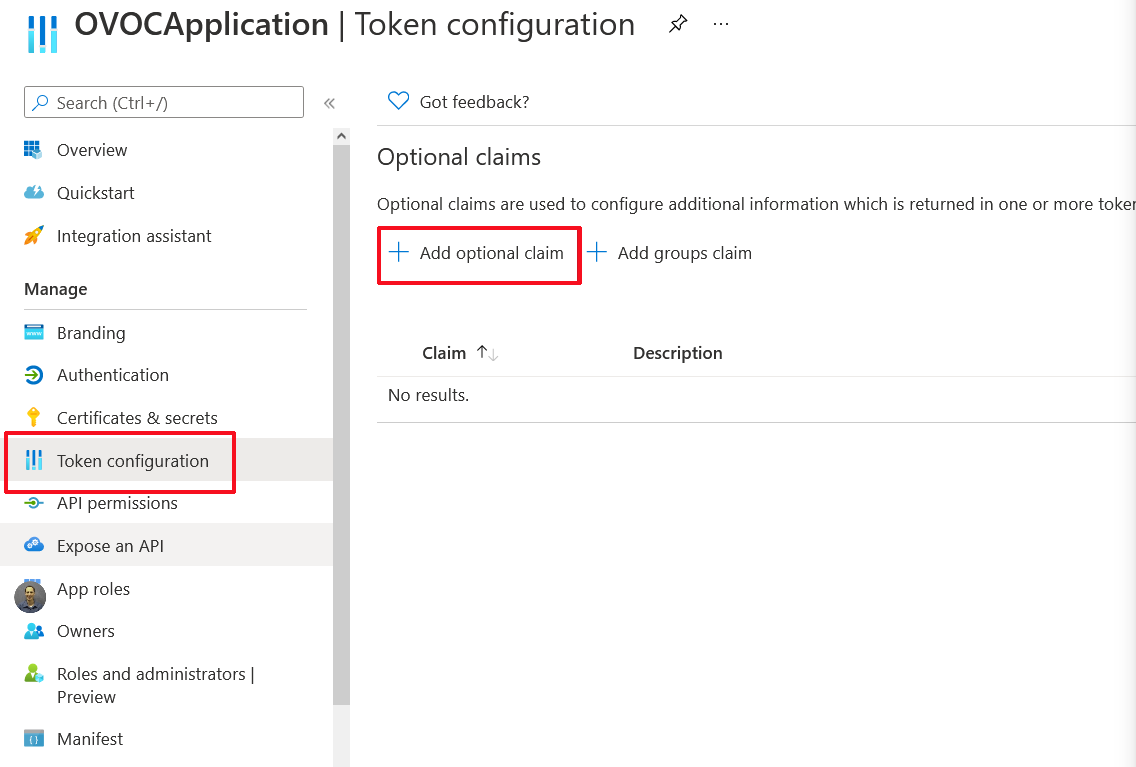
| 17. | Select Add optional claim. |
| 18. | Under Token Type, select ID. |
| 19. | Under Claims, select the upn check box. |
| 20. | Click Add. |
Add Optional claim
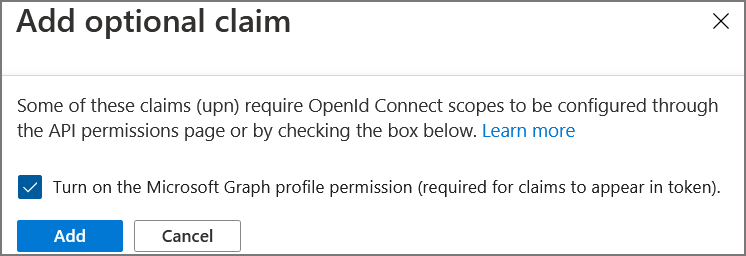
| 21. | Select the Turn on the Microsoft Graph profile permission check box and then click Add. This adds the Profile permission to the API permissions list. |
The new claim is displayed.
New UPN Claim
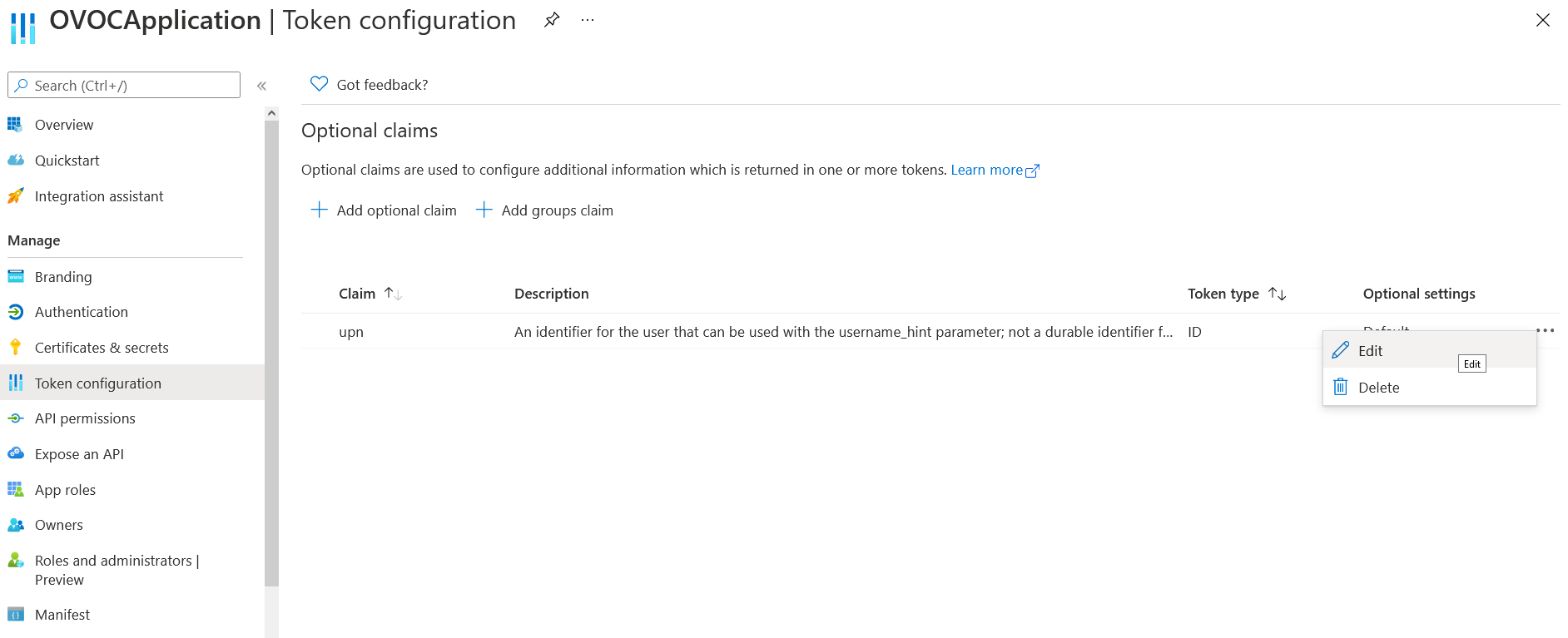
| 22. | Right-click the newly added token and select Edit. |
Edit Optional Claim
| 23. | Under Edit UPN (ID token), select Yes to Externally authenticate guest users (users that are not members of the organization's Azure defined groups). |
Edit UPN (ID token)
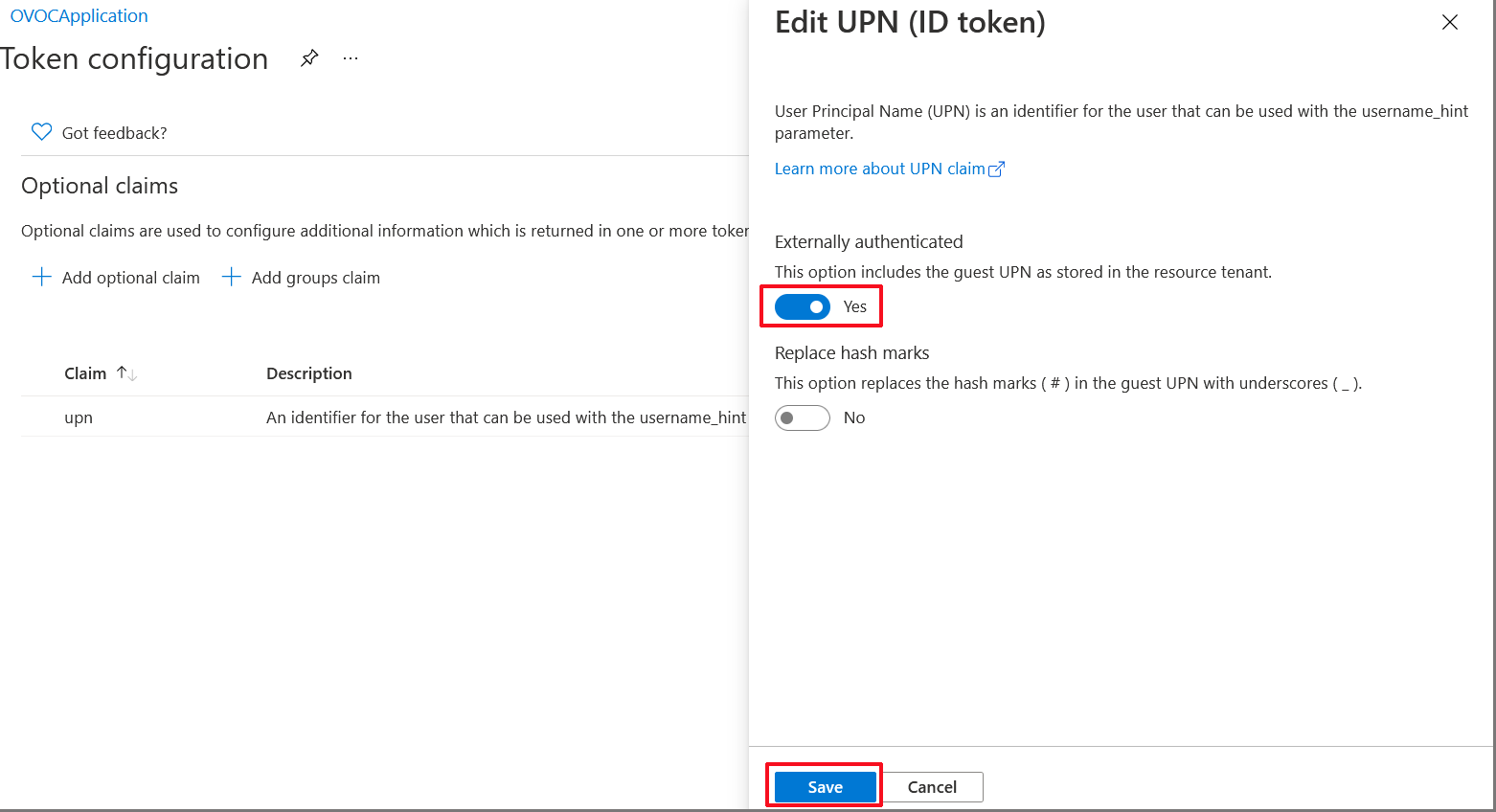
| 24. | Click Save. |
| 25. | In the Navigation pane, select API permissions. |
API Permissions
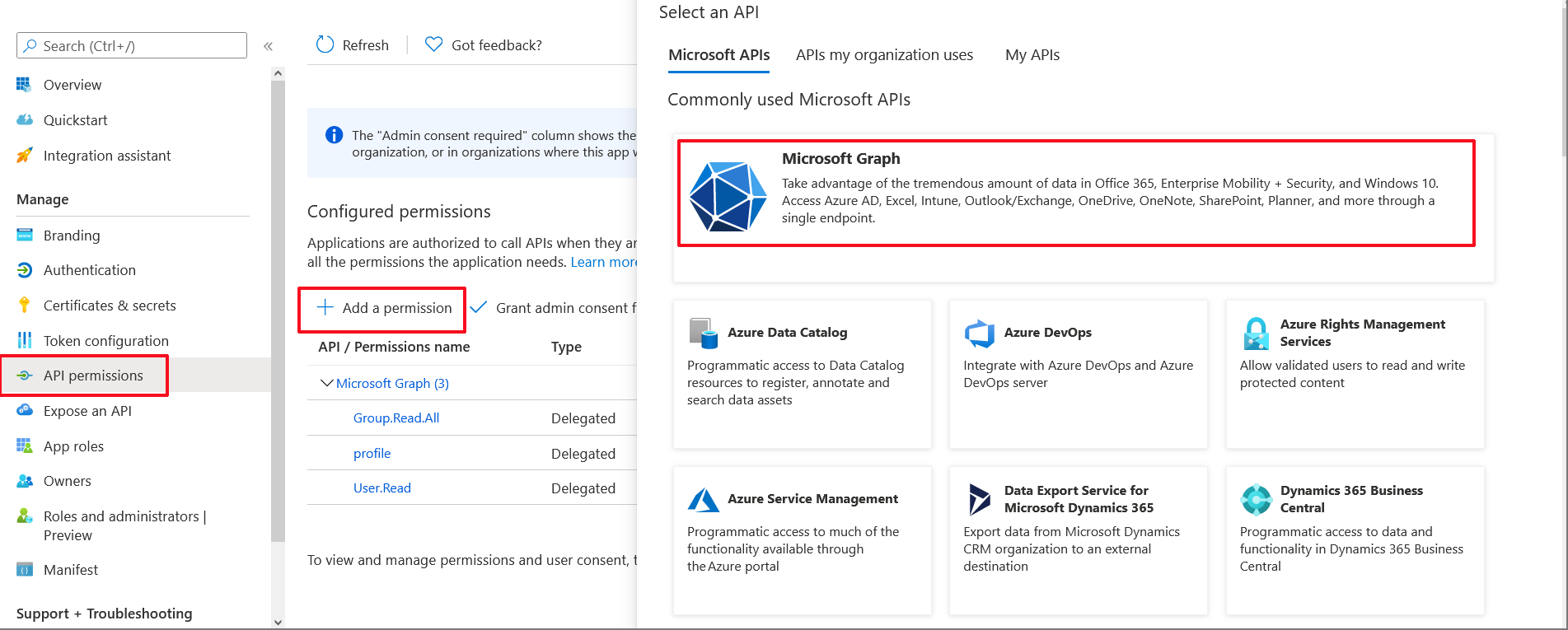
| 26. | Click Add a permission and then click the Microsoft Graph link. |
Delegated permissions
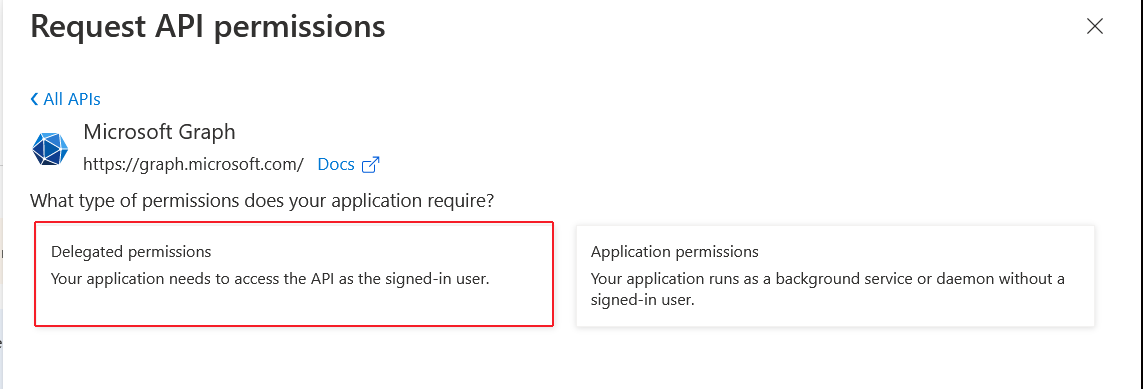
| 27. | Click Delegated permissions. |
Microsoft Graph Permissions
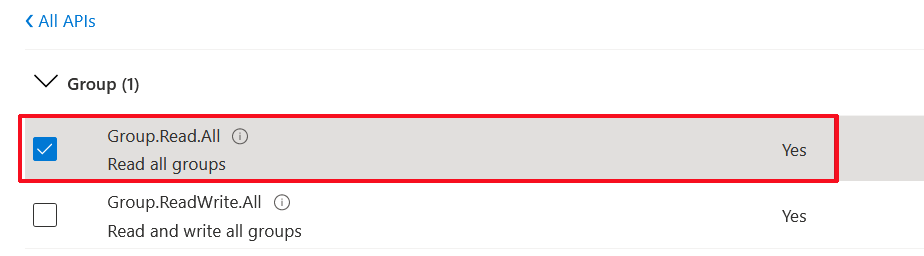
| 28. | Select Group.Read.All for OVOC to read permissions from all user groups defined for the tenant, and then click Add permissions. |
| 29. | Add another Delegated permission User.Read.All and then click Add permissons. |
Delegated permissions

The configured API permissions are displayed.
Configured API Permissions
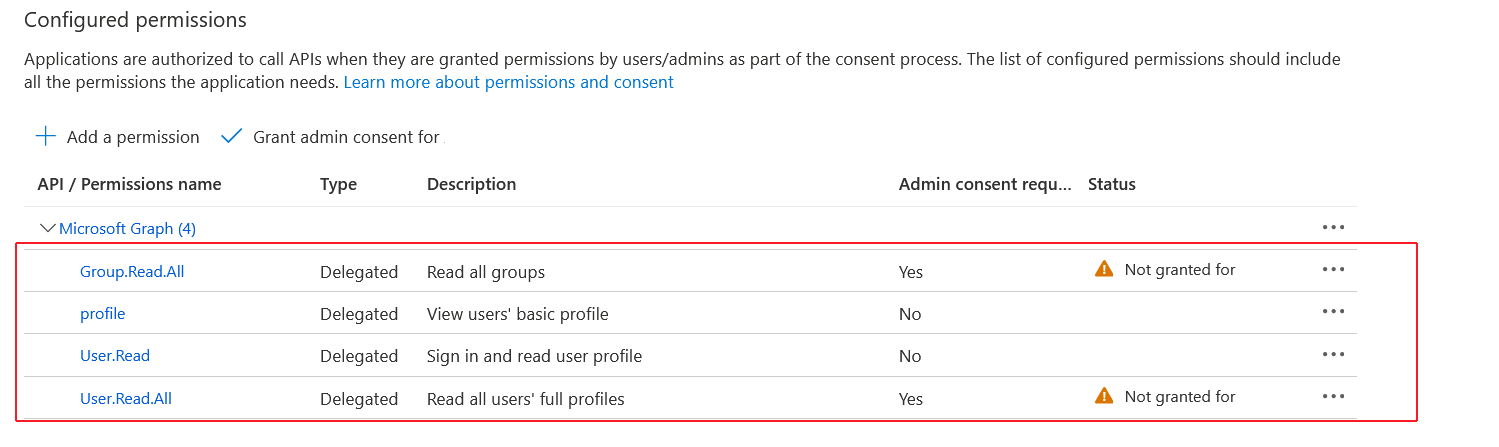
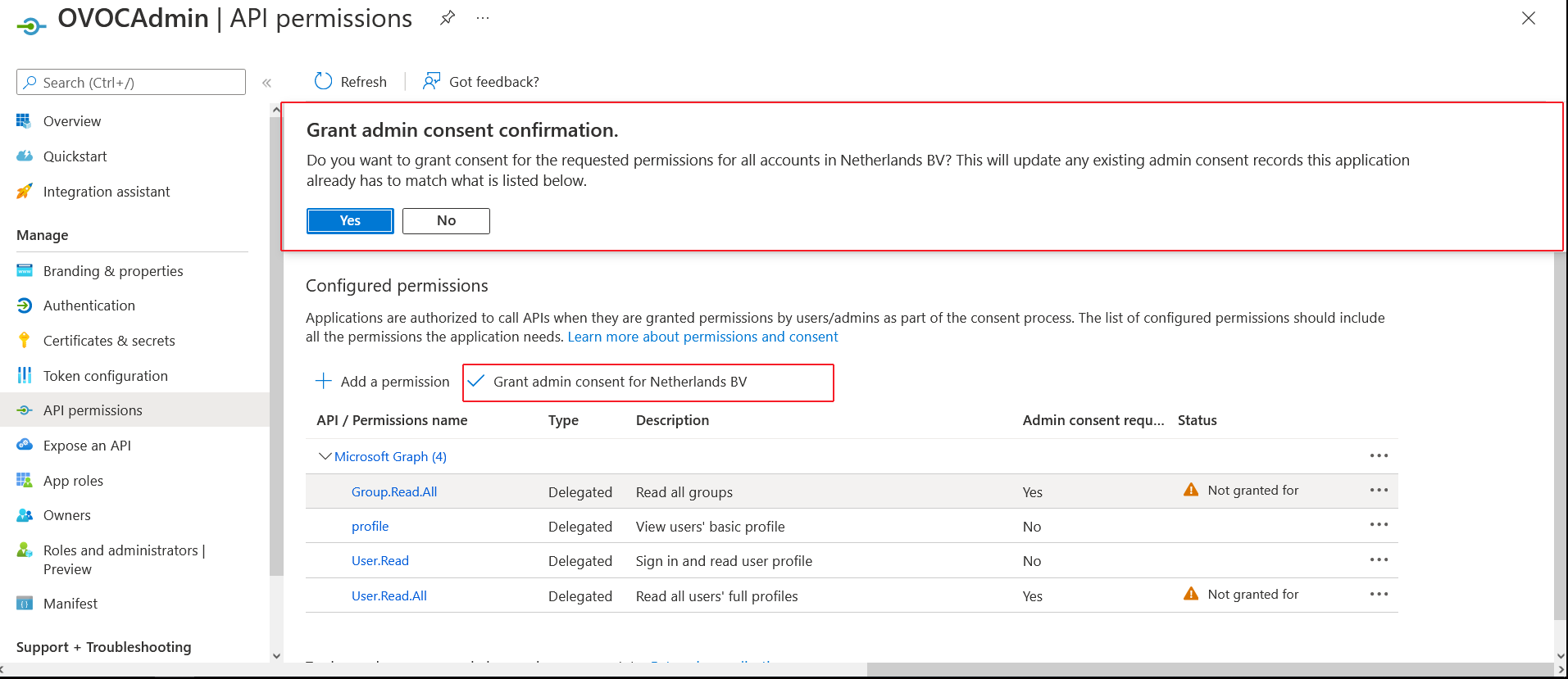
| 30. | Click Grant admin consent for <Tenant_Name> link to grant consent for the requested permissions for all accounts for this tenant, and then click Yes to confirm. |
Grant Admin Consent for all Accounts
| 31. | In the Navigation pane, select the Overview page for the application. |
Overview Page
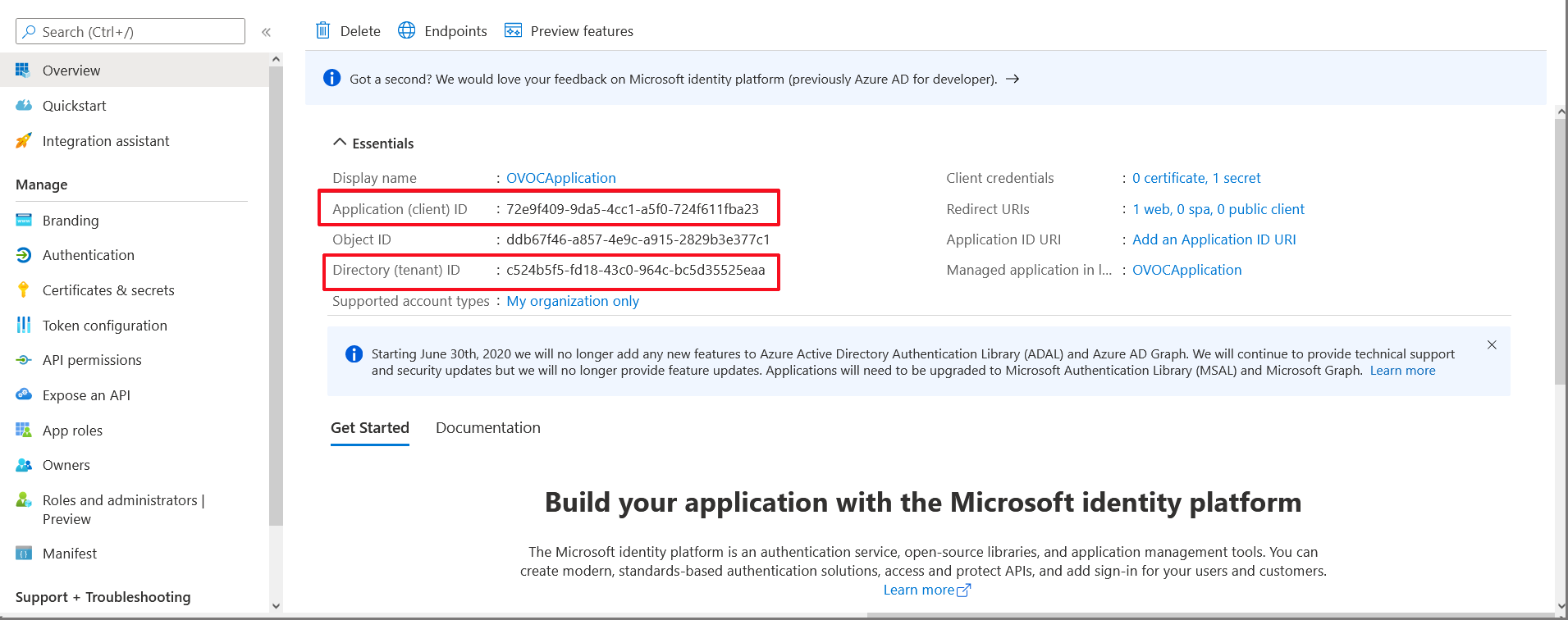
| 32. | Note the following values as they must later be configured in Configuring OVOC Web Azure Settings - Single Tenant Setup |
| ● | Application (client) ID |
| ● | Directory (tenant) ID |
| 33. | Add Main Tenant Azure groups and add members as described in Create Azure Groups and Assign Members |
| 34. | Configure Azure settings in OVOC Web as described in Configuring OVOC Web Azure Settings - Single Tenant Setup |